*** NOTE: ALL INFORMATION IS ACCURATE AT DATE OF PUBLISHING ***
One of the most important areas for a CRM System Administrator to spend time is on Security Roles. You need to make sure users have access to the right entities, and can perform the right actions. For each entity a user can have a combination of rights to Create, Read, Write, Delete, Append, Append To, Assign and Share.
For some sections in the Security Roles there are additional Miscellaneous Privileges. Some are pretty obvious what they are for, others, not so much! In this four part blog post we’ll take a look at those additional settings. Unlike the Key for entities (None, User, Business Unite, Parent: Child Business Units, Organization), some of these settings are either On or Off.
NOTE: this post series is based on Dynamics 365 CRM so you may find that some of them don’t exist in your environment if it’s an older version.
First, let’s look at settings under Core Records.
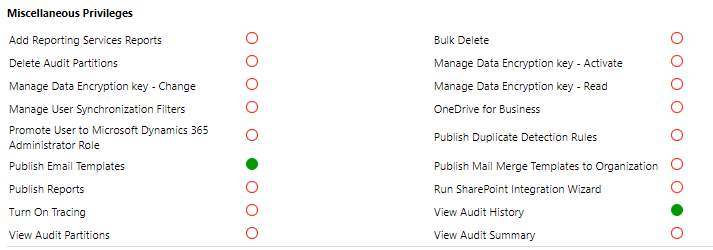
Add Reporting Services Reports
Assigning this privilege allows a user to upload an SSRS report to CRM. This is done by selecting Existing File as the Report Type. Without the access, they will still see the option available, be able to browse out to the report file, but when saving will be presented with an insufficient privileges message and prevented from adding the report.

Bulk Delete
The bulk delete feature allows users to create rules for which records to remove from your CRM environment. Without this privilege, users will not see this feature available from the delete command in the ribbon. If they have access to Settings and can still get to the Data Management area, they will be able to see any Bulk Record Deletion jobs, but will not be able to add new ones.
Delete Audit Partitions
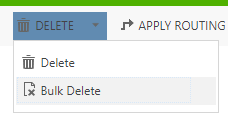
If you have auditing turned on in your CRM environment and are tracking a lot of fields your audit logs can get pretty large. These are partitioned by quarters. If you start running out of space, deleting them can help free up some of that space. The ‘Delete Audit Partitions’ privilege allows a user to go to Settings, Auditing, Audit Log Management and delete a log partition (excluding the quarter you are currently in).
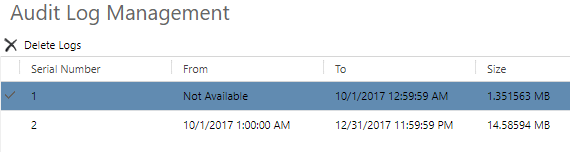
Manage Data Encryption key – Activate, Manage Data Encryption key – Change, Manage Data Encryption key – Read
The three settings above all pertain to Data Encryption keys for your instance. This allows you to lock and unlock the instance, among other things. It’s typically not something you would need to be doing, so for more information, check out this article. From Settings, Data Management, Data Encryption, an encryption key can be changed. These three privileges will allow someone to either Activate a new key, Change a key, or Read information on the screen below. Be careful with these permissions!
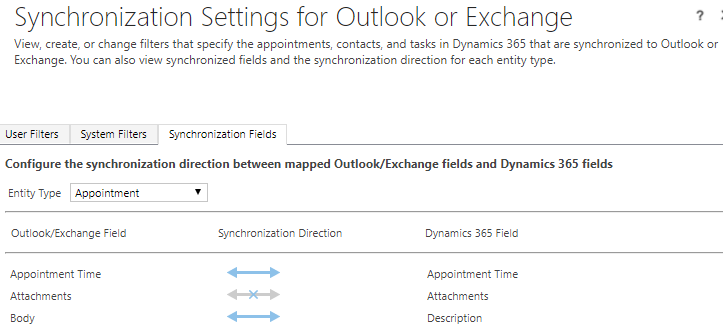
Manage User Synchronization Filters
From Settings, Administration, System Settings, you can go to Synchronization, then change the settings for the fields you wish to sync for appointments, contacts and tasks. As a system administrator you can then control the data that goes between Outlook and CRM. The privilege for ‘Manage User Synchronization Filters’ can be turned off which will prevent users from setting up their own sync settings.
OneDrive for Business
If you have OneDrive for Business, users can create and manage their own private documents, which can then be accessed from Dynamics 365 CRM. Without the OneDrive for Business privilege, users will not see the OneDrive option throughout CRM.
Promote User to Microsoft Dynamics 365 Administrator Role
This setting is not activated on the System Administrator Security Role and cannot actually be given to another Security Role. It appears that a user has to have an admin role assigned within Office Admin before they are able to promote another user to Admin within CRM. Clicking on the Promote To Admin button will assign the System Administrator security role to the user.
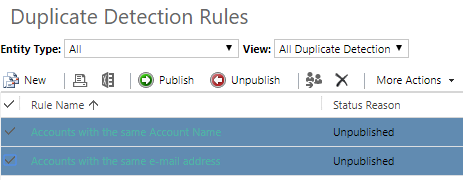
Publish Duplicate Detection Rules
Duplicate Detection Rules can help prevent users from adding duplicate records to your CRM environment. You can provide a user with access to create new rules from Settings, Data Management, Duplicate Detection Rules, but if the ‘Publish Duplicate Detection Rules’ setting is turned off, they will no longer see the Publish or Unpublish options available.
Publish Email Templates
Users are able to create Email Templates in CRM. If a security role has Publish Email Templates enabled, users will be able to make that template available throughout the organization for others to use.
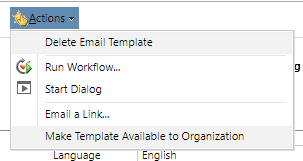
Publish Mail Merge Templates to Organization
Users are able to create Mail Merge Templates in CRM. If a security role has Publish Mail Merge Templates to Organization enabled, users will be able to make that template available throughout the organization for others to use.
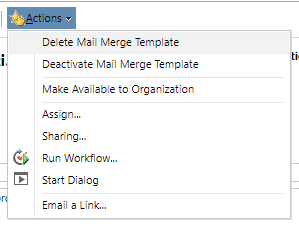
Publish Reports
Users are able to create reports using the report wizard. If a security role has Publish Reports enabled, users will be able to make that report available throughout the organisation for others to run.
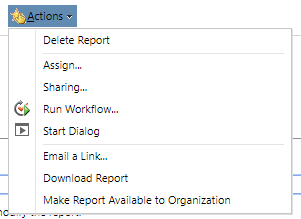
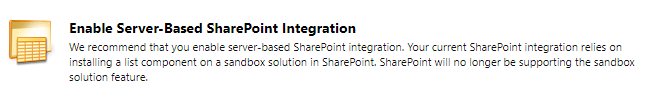
Run SharePoint Integration Wizard
With this privilege a user can set up the SharePoint Integration Wizard (which is a one time only process).
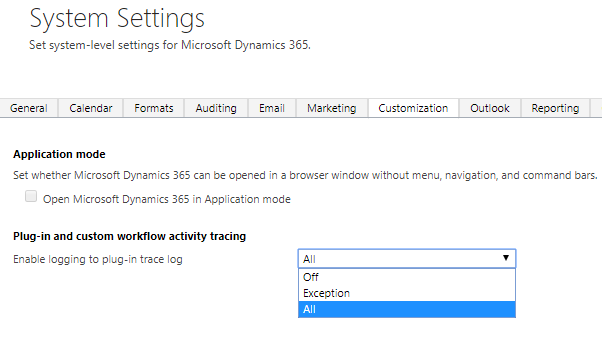
Turn On Tracing
Trace logging can be turned on to track and troubleshoot issues with plugins and workflows. The setting to turn on tracing can be found in Settings, Administration, System Settings then Customization.
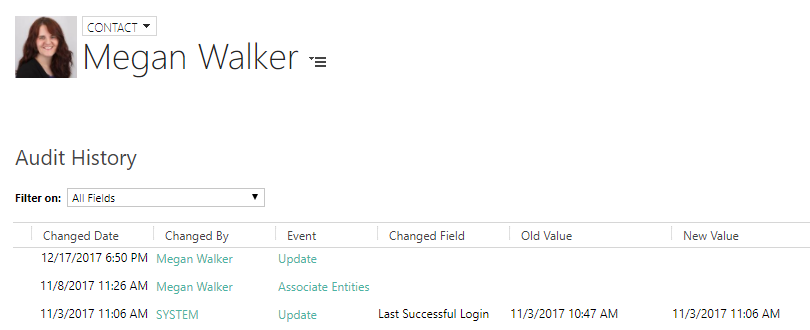
View Audit History
If this privilege is not given, users will not be able to view the Audit History for any entity which is auditing turned on.
View Audit Partitions, View Audit Summary
The last two items for Core records Miscellaneous Privileges are for Audit trails. Audit Log Management will not be visible unless View Audit Partitions is active. This allows you to view the partitions mentions in the Delete Audit Partitions mentioned earlier in the post. Audit Summary View provides a list of transactions across records and users, allowing you to filter and review by Event or User as needed.

Read the next in the series:
Miscellaneous Privileges on Security Roles – Part Two
Miscellaneous Privileges on Security Roles – Part Three
Helpful Info
This link from Microsoft provides a mapping of the security role user interface to the privilege names.
Security role UI to privilege mapping
Check out the latest post:
Assign Records To A User Or A Team From Your Custom Page
This is just 1 of 571 articles. You can browse through all of them by going to the main blog page, or navigate through different categories to find more content you are interested in. You can also subscribe and get new blog posts emailed to you directly.

Great series of articles Megan – much appreciated.
Thanks Simon! Hope they were helpful in some way. I learned a lot going through all of the settings.